📜 Description
The chatroom where all hackers used to hang out was found to contain a serious 0-day vulnerability. There is still no official explanation of how the vulnerability can be exploited, can you figure it out?
~ The flag can be found in the file: /tmp/flag.txt
🕵️ Recon
The application allows us to send messages to recipients by sending a JSON with the attributes to and msg. Example : {“to”:“owne”,“msg”:“hello !”} The application will then save our message as a draft using the following code:
|
|
The file name is created using ${Date.now()}_${this.to}, and the application writes the content of our msg attribute into the file.
The application will then render the index.js file using message.msg as the template variable.
|
|
🚧 POC
The makeDraft() function is vulnerable to File Overwrite because if an attacker use ../index.ejs as value of to, this.file will have the value index.ejs
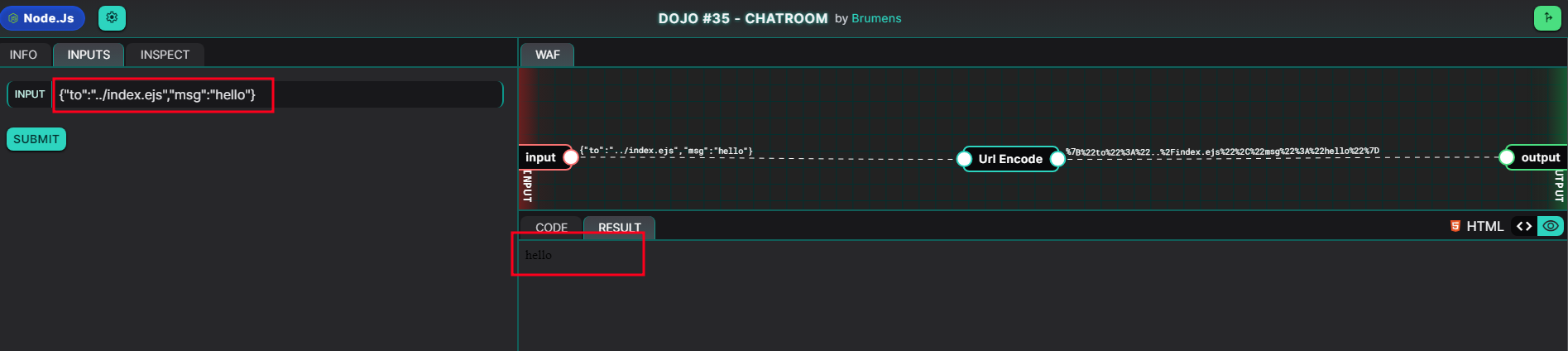
The index.ejs file has been overwritten!
Now, since we control the index.ejs file, which will then be rendered by the server, we can inject a template that allows us to read files on the server, such as <%-include('/tmp/flag.txt') %>
If we send the payload {"to":"../index.ejs","msg":"<%-include('/tmp/flag.txt') %>"} :
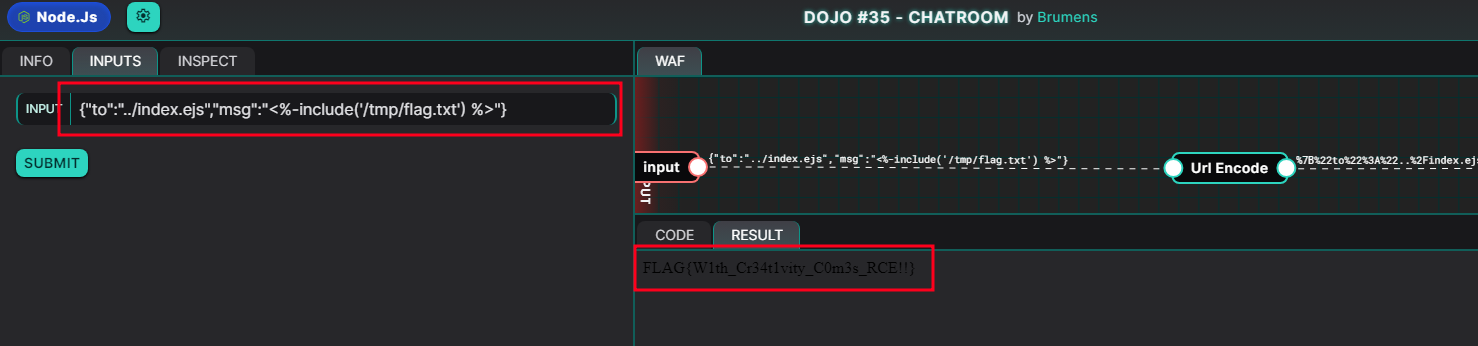
We can read files on the server!
Thanks Brumens for this challenge!
🔐 Mitigations
Input validation is a frequently-used technique for checking potentially dangerous inputs in order to ensure that the inputs are safe for processing within the code, or when communicating with other components. When software does not validate input properly, an attacker is able to craft the input in a form that is not expected by the rest of the application. This will lead to parts of the system receiving unintended input, which may result in altered control flow, arbitrary control of a resource, or arbitrary code execution.
📚 References
Arbitrary code execution CWE-20: Improper Input Validation CWE-94: Improper Control of Generation of Code (‘Code Injection’)