📜 Description
A new tool has recently been published, designed to generate beautiful AI images based on your given prompt. We have also made sure that it works to upload files if the prompt is in XML format! Will you be able to find the flag?
~ _The flag can be found in the file: /tmp/flag.txt
Note: The docker application do not have access to the internet
🕵️ Proof of Concept
The application allows us to send XML
|
|
Then the application base64 decode our input and it check if it is UTF-16 or not :
|
|
So If we send an XML payload in UTF-16, we can bypass the filter
|
|
Then convert it to UTF-16 using iconv :
|
|
Then :
|
|
We can now send the payload :
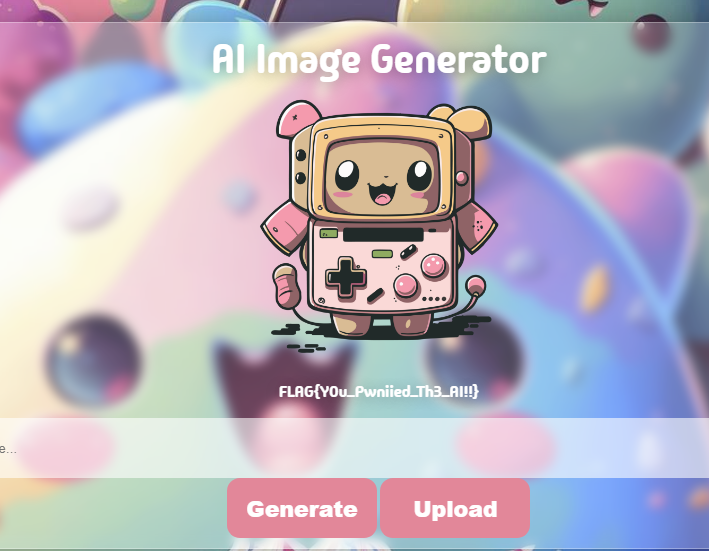
Thanks Pwnii & Brumens for the challenge !
🚧 Impacts
XXE attacks can be used to access sensitive information from the application or from the server on which it is running. For example, an attacker might use an XXE attack to read sensitive files from the file system, send HTTP requests to other servers, or even execute commands on the server.
🔐 Mitigations
XXE vulnerabilities can occur when an application processes XML input without properly validating or sanitizing it. This can allow an attacker to inject malicious code into the XML input, which is then executed by the application.
To prevent XXE attacks, it is important to properly validate and sanitize all XML input to ensure that it does not contain any malicious code. This can be done using techniques such as input validation, input sanitization, and input whitelisting. It is also important to keep the application and its dependencies up to date to ensure that any known vulnerabilities are patched.
📚 References
PortSwigger - XML external entity (XXE) CWE-611: Improper Restriction of XML External Entity Reference